MS Teams
MS Teams is a collaboration platform that provides “sites” for projects. Each site can store and share documents and enables collaborative editing on the documents. Sites also have discussion board channels (similar to Slack or Discord) and can be used to host secure meetings (similar to Zoom).
Types of uses
- Collaboration in groups or teams
- Document storage, sharing, and collaborative editing
- Group discussions and chats
- Secure synchronous audio/videoconference meetings
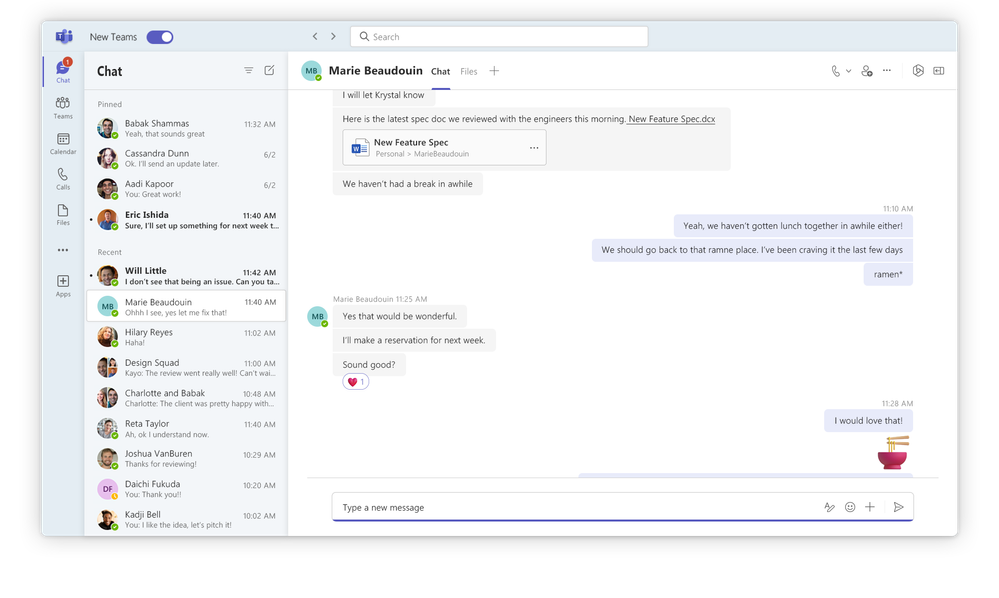
What it looks like
Considerations before using this tool
Safety
How will you deal with any disruptive behaviour that may occur in an online meeting or during online collaboration? How will you respond if a student, faculty or staff member has a negative experience while using this tool? How can you mitigate any online harassment that might take place?
Comfort and Ease of Use
Does this tool suit your specific needs? Do your students/colleagues have access to it? What protocol will you follow to promote respect in your online meeting or during a collaborative activity? What do you want students, faculty or staff to do if they feel uncomfortable in this online space?
Security
How will you comply with relevant data retention rules?
Pedagogy
How can this tool efficiently serve your purposes?
Support available
- UService (IT)
- UCalgary: MS Teams Directions and FAQ
- Taylor Institute: consultations: one-on-one consultation, learning technology coaches
- Microsoft Support:
Useful information and tips
- UCalgary: Microsoft Teams recommended for online meetings (April, 2020)
- MS Teams: Online & remote classrooms
- Microsoft Teams Tips and Tricks for Teachers
About this tool
Name: Microsoft Teams
Vendor: Microsoft, Inc.
Website: https://teams.microsoft.com
Cost: Free (campus license provided)
Status: core platform.
Approved for:
Level 1 Data: Public
Public is defined as:
- Information deemed to be public by legislation and/or under University policy
- Information in the public domain
Examples include:
- names of employees and
- business contact information
- job profile
- salary range
- discretional benefits
- relevant education
- names of registered students and
- dates of registration
- program of registration
- degree awarded
- convocation date
- annual reports
- public announcements
- telephone directory
- published research data
Level 2 Data: Internal Use
Internal Use is defined as:
- Information not approved for general circulation outside the University
- Information the disclosure or loss of which would inconvenience the University although it would unlikely result in financial loss or reputational damage
Examples of this include:
- internal memos sent to all members of a department
- minutes of department meetings that are circulated to all members of a department
- unpublished research data
- anonymized or de-identified human subject data
- library transactions and journals
Level 3 Data: Confidential
Confidential is defined as:
- Information that is available only to authorized persons
- Information the disclosure or loss of which could seriously impede the University’s operations
- Information the disclosure or loss of which may:
- adversely affect the University’s operation; or
- cause reputational damage; and
- obligate the University to report to the government or other regulating body and/or provide notice to affected individuals.
Examples include:
- faculty/staff employment applications, personnel files, date of birth, health information and personal contact information
- admission applications
- student enrollment status
- donor or prospective donor name and contact information
- information commonly used to establish identity such as a driver’s license or passport
- contracts
- intellectual property
- authentication verifiers including:
- passwords
- shared secrets
- cryptographic private keys
Level 4 Data: Restricted
Restricted is defined as:
- confidential; and
- subject to specific privacy and security safeguards under law, policy or contractual agreement.
- Information the loss or disclosure of which could cause severe harm to individuals or the University
- Information the loss or disclosure of which may obligate the University to report to the government or other regulating body and/or provide notice to affected individuals.
Examples include:
- payment card information including:
- PAN
- cardholder name
- VV2/CVC2/CID
- health information when it can be linked to an identifiable individual including:
- information about health status
- diagnostic,treatment or care information
- payment for health care
- identifiable human subject research data
- information that is subject to special government requirements in the interests of national security
For more information, please refer to the University of Calgary’s Information Security Classification Standard.
Software license: Commercial, proprietary
Hosting: Servers hosted by vendor

